
Today’s virtual world faces hundreds of cyber threats, and they try to penetrate cybersecurity programs every day. To address possible breaches, many organizations have adopted identity and access management (IAM) systems, security frameworks that identify and manage digital users.
However, traditional IAM solutions may not be well-equipped to detect more sophisticated attacks. With exposed data, companies must fortify their cyber defenses to prevent threats or mitigate damages.
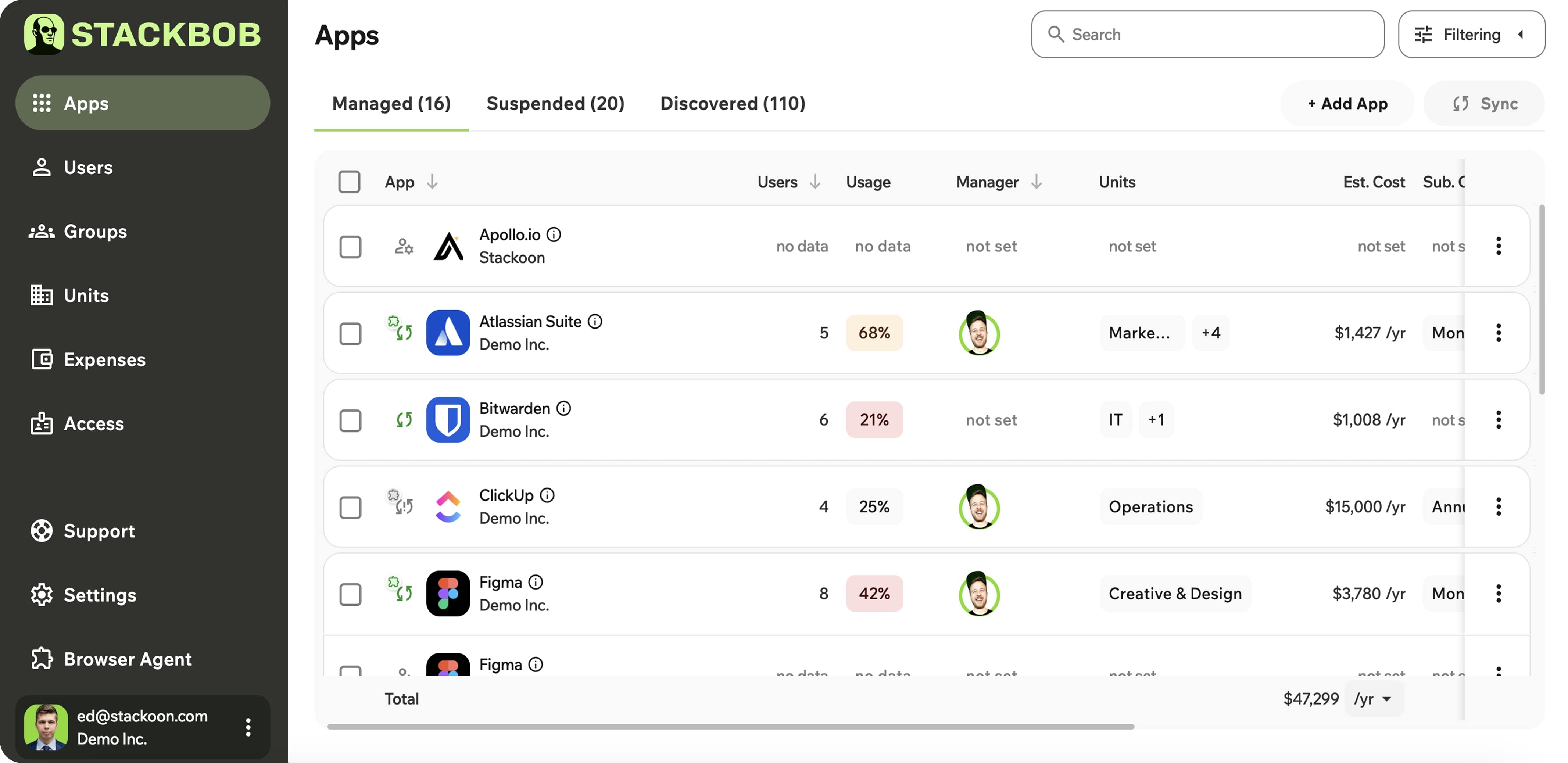
Agent-based IAM like StackBob feature the necessary protection that can fill the gaps left by legacy systems. These platforms not only offer single sign-on (SSO) tools but also provide solutions that bring visibility and real-time control across an organization’s digital environment.
Bridge Limitations Through Agent-Based IAM
In many academic cybersecurity programs, aspiring professionals are taught that traditional identity and access management solutions safeguard digital identities through role-based logins and passwords. These cybersecurity programs or software operate within fixed policy frameworks that can’t track dynamic actions, so unprecedented activities are usually left unchecked until it is too late. With agentic identity and access management solutions, risk is constantly assessed in real-time using other signals, so the threat is greatly reduced. Discussions in these areas introduce students of cybersecurity programs to the role of artificial intelligence (AI) in identity and data protection.
Meanwhile, industry practitioners and organizations can explore advanced software to reinforce security measures at every tech stack. Unlike traditional IAM that rely on static access controls, follow confined predetermined roles, or have delayed threat detection, IAM systems such as StackBob utilize autonomous agents that continuously adapt from user context and behavior in real-time. This visibility closes persistent gaps that traditional IAM systems leave vulnerable.
Core Features of Agent-Based IAM
- Identity Governance: Many IAM tools connect your team with every single system they use, including those without SCIM API or SAML SSO. This process ensures each account is managed and consolidates fragmented identity data into one centralized view.
- Zero-Trust Model: Modern IAM utilizing agents verifies every access attempt through continuous session-based validations and least privilege permissions. This approach eliminates the perimeter-based weaknesses found in traditional IAM architectures.
- Password Management: Some agentic IAM tools generate strong, unique passwords for every tool and store them in an encrypted vault, which can only be accessed through strict authentication steps. This minimizes the risks of leaked data, which affects around 93.64 million accounts, according to Statista.
- Authentication: IAM implementations use several authentication factors to corroborate digital identities. This process relies on those contextual and behavioral factors, like user patterns, location, or devices logged, to reduce the risk of unauthorized access or compromised accounts.
- Constant Monitoring: According to CompTIA, around half of cybersecurity professionals believe that AI helps analyze user behavior and forecast breaches. With agentic IAM, systems can scan actions regularly and close lagging detection issues from traditional IAM systems without being too invasive.
- Automated User Access: Agent-based solutions instantly manage access throughout the user lifecycle. This level of automation minimizes the manual process of access updating and guarantees consistent control.
- Auditing and Reporting: Most programs keep a detailed log of all access events and offer data-driven analytics across every connected system. This proactive recordkeeping instantly helps organizations provide evidence during audits.
Implementation Considerations for Agentic IAM
Agent-based identity and access management solutions offer well-rounded tools that help face modern cyber threats, making them some of the most promising cybersecurity programs in the market. With that in mind, it is best to evaluate the following points to determine whether it matches your organizational needs:
- Scalability and Cost: Agent-based IAM systems are typically built to scale with a company’s growth, which is why many products in the market offer flexible pricing. This can range from free plans for small organizations to custom pricing for enterprises, enabling organizations to select the right cost that matches their budget without sacrificing advanced features.
- Integration: Agentic IAM complements other cybersecurity software and is also compatible with many productivity apps. However, some integrations may require other requirements that could prompt occasional manual interventions, so IT teams must check if their existing systems are suitable with IAM solutions.
- Data Privacy and Maintenance: Because most IAM tools continuously track user and device activities, organizations must double check if these meet internal and regulatory compliance standards regarding data privacy. In addition, IT teams must perform regular maintenance to ensure transparency and responsible monitoring.
Despite being a new name, StackBob has entered the IAM market strongly by delivering reliable products and services. In fact, even Google approves of StackBob. Moreover, its case studies and feedback-driven improvements demonstrate its commitment to protect organizations.
Strengthen Defenses Long-Term With StackBob
As an agentic identity and access management system, StackBob provides several benefits to different companies. It automates role and access controls to help teams manage information more easily. Moreover, StackBob streamlines app security, monitors activities in real-time, and shields digital identities to ensure maximum protection and program utilization while saving on unnecessary costs.
Cybersecurity programs like StackBob are becoming more vital to organizations as digital threats increasingly level up their breaching capabilities. Old-school IAM measures alone may no longer be sufficient in anticipating these modern dangers. Now, more than ever, companies need agent-based IAM such as StackBob not only to fill in and close security gaps left by legacy systems but also to future-proof digital environments.
